In addition to traffic distribution, Amazon Route53 health checks can be configured for each record to ensure traffic is only sent to healthy nodes. The next figure shows the health check configurations for our pair of WireGuard VPN servers in an AWS Local Zone:
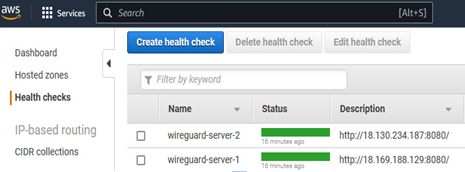
Figure 6.17 – Amazon Route53 health checks for two WireGuard VPN servers
You will notice the health check is querying http://<ip-address>:8080/. Because WireGuard is a UDP service on port 51820, there is no health check type that can directly test it. Therefore, we need to configure a small web service on each WireGuard instance that answers the health check.
Let’s go over instructions for setting up a basic web service on a Linux server.
On a Debian-based Linux distribution such as Ubuntu, input the following:
sudo apt install apache2 -y
systemctl enable apache2
systemctl start apache2
echo “<html><body>healthy</body></html>” > /var/www/html/index.html
On a Fedora-based Linux distribution such as Amazon Linux 2023, input the following:
sudo yum install httpd -y
systemctl enable httpd
systemctl enable httpd
echo “<html><body>healthy</body></html>” > /var/www/html/index.html
Now you need to set the Security Group for the EC2 instances to allow port 80 traffic to pass through, but you don’t want to expose it to the entire internet unnecessarily. Fortunately, AWS provides managed Prefix lists for situations such as this:
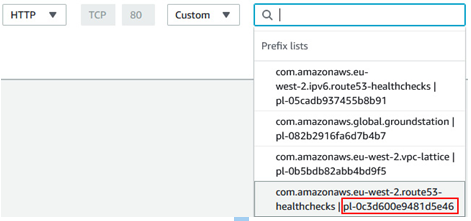
Figure 6.18 – Allowing HTTP only from the Amazon Route53 health check service
When editing the Security Group, select the Custom type. Then, scroll down to the bottom of the choices in the drop-down menu until you find com.amazonaws.<region>.route-53-healthchecks. Select it, and the prefix list ID will be entered into the rule. This will allow the health checkers in all regions to query your instance via HTTP.
By default, the health checkers are only looking for an HTTP response code 200 to consider the instance healthy. This isn’t perfect, but at least proves the instance is alive on the network and the operating system is running in general.
A more sophisticated responder could be built as a Python script invoked as a service in a systemd unit file. Using subprocess to check the state of the VPN interface and http.server to reply to queries, the response could contain whatever information you want in the response, which the Amazon Route53 health check can parse to determine things such as whether the WireGuard service is functional but at capacity in terms of client connections.

