Outposts servers require two physical connections to perform properly and the cables needed for this connectivity are provided to customers with their Outposts server. The two connections are used to segment traffic according to traffic class and are not intended for redundancy.
These connections are not required to be on a common network. The cable provided for this use is a QSFP+ to 4xSFP+ breakout cable. The QSFP+ interface plugs into port 3 of the Outposts server. The SFP+ interfaces plug into the customer switch side with SFP+ interface 1 used for traffic labeled 1: LNI traffic and SFP+ interface 2 for traffic labeled 2: service link traffic. Note that SFP+ interfaces 3 and 4 are not currently used in an Outposts server deployment.
The customer switch port for the service link should be an untagged access port with routing capabilities out to service link endpoints in the AWS region and the Outposts registration endpoint in the AWS region. This connection must also have public DNS available for resolution of service link endpoints and for proper registration with the Outposts registration endpoint. Note that TCP and UDP ports 443, along with UDP port 53, need to be allowed and that NAT is allowed between the Outposts server and the registration endpoint.
Service link
Outposts Server provides a local Layer 2 connection compared to requiring Border Gateway Protocol (BGP) through a routed network for the service link.
The maximum throughput over any one Outposts Server service link is 500 Mbps. Customers can leverage multiple Outposts servers to increase the effective throughput back to the region according. For example, three Outposts servers could be used to achieve 1.5 Gbps throughput to the region in aggregate.
The customer switch port for the LNI traffic should be a standard access port to a VLAN on the customer network. Customers with more than one VLAN must configure the port to accept multiple MAC addresses as each EC2 instance launched will use a unique MAC address, and also configure all ports as trunk ports. Note that you will need to use trunk mode for your LNI; you will be responsible for any VLAN tagging needed at the EC2 operating system level as Outposts servers do not perform VLAN tagging.
Logical network interfaces (LNIs)
Unlike the shared LGW found in an AWS Outposts Rack deployment, Outposts Server enables each EC2 instance to communicate directly with on-premises infrastructure by way of an LNI:
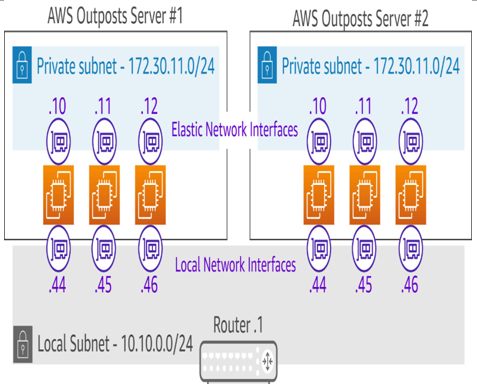
Figure 5.22 – LNIs on an AWS Outposts server
The LNI having direct communications through the LAN means customers don’t need to set up routing or gateways for the Outposts servers to communicate locally. Customers are responsible for ensuring that proper multi-network routes exist on the EC2 instances to allow for communications through the LNI and also through the standard Elastic Network Interface (ENI), which is automatically provided to an EC2 instance for communication to the VPC. The ENIs on an Outposts server behave identically to the way ENIs work in-region. The ENIs provide connectivity to public or private VPC endpoints in the parent region.

